AyMINE – Technical documentation
Interfaces to other systems
Enterprise Architect Connector
CalDav, WebDav using Sabre
Business excelenece
Balance Scroecards
Task & Project Control
- Helpdesk ticket - reply to customer
- Test
- Qualification of user or contact
- Project role
- What makes up the methodology / QMS
- dragdrop
- Location
- My areas
- Kanban Task Overview
- Personal Task
- Internal helpdesk
- Customer Care Centre
- Project baseline
- Return project plan by baseline
- Project Schedule
- Processing time sheets
- Records managed by a project
- Activation buttons
- Why some data can't be deleted
- Starting events
- Qualification of user or contact
- task_taskobjects
- Project
- Reminders and Messages
- eventobj_raisingevents
- decision_decobjects
- eventobj_startingevents
- eventobj_eventbuttons
- Type of tests
- Deal management
- FMEA - Detection
- FMEA - Features
- FMEA Methodology | AyMINE
- FMEA - Occurence analysis
- FMEA Severity analysis
- FMEA
- Management of responsibilities - RACI Matrix
- RACI Matrix for Project
- Improvements and Preventive Measures
- Notice – example of use
- tskproblem_terminology
- 8D report
- Task Scheduling
- Administration of the Task Management Module
- Adminitration of areas, projects, calendars
- Discussion
- GDPR and record of qualifications
- System rights for the task management module
- Project Planning
- Employee Tasks
- Incident and Quality Issue Management
- Collaborative Resolution of Multiple Problems
- List of business areas
- Required qualifications
- Plan template / strategy
- Decision
- Configuration Package
- Record template
- Change management process in a project
- Task list
- Requirements
- Team Member
- Right to Manage Qualifications
- Input requirements
- Obligation
- Competencies and Skills
- Problems, tickets and their management
- Meeting
- Package definition
- Phrases and terms
- Data Area
- Risk
- Task
- Business event
- Task, project & quality management
- Records and protocols
- Directives and Policies
- Events
- Risk Pattern
- Information
- Project definition
- Activity log
- eventinstances
- Personal calendar
- Objects of decision making
- Event activation buttons
- Objects affected by the problem
- Variant decision-making
- Recorded activities
- Self-Reminders
- QMS and Task Management
- Objects related to the task pattern
- Effect of the task on the right to modify the atta
- Level of Competence
- Manager approval with the task report
- Region / project / methodology
- Manage your marks
- tskdefusertask
- Quality Management System (QMS)
- tsktask_batasks
- Project Team
- Events and meetings
- Events and meetings
- List of event instances
- moduleclientoptions
- Processed objects
- Mark patterns
- Notification events
Interprocess management
Human Resources
- hrstcontract
- roles
- Human resources
- Digital Personnel Archive
- Personalistics – User Permissions and roles
- Registration of job seekers
- Manage department / division data
- Job Position
- Worker
- Worker overview
- An overview of your staff
- Responsible HR Manager
- Synchronizing staff and system users
- modulesafety
Asset Management
- Products, assets and sales
- Tendering and purchasing
- Analytical model
- Product Supplier
- Product Categories
- Product or Product Property
- Project Goal
- Business Offer
- Offers summaries
- Recalculate bid
- Offer and Price Access Rights
- Creating and processing orders
- System order status query
- Order Reports
- Pricing
- Pricing – volume discounts
- Products and Goods
- Product status and change
- Product Units
- Quality criteria
- Why are the Quality criteria usefull
- DFMEA - Product FMEA
- Hara | Hazarad & Risk Analysis
Customer Relationship - CRM
- Contacts and directories module (
- System Permissions and CRM Module Settings
- Customer Order Overview
- Address books
- Address book list and management
- Privacy policy
- Send bulk messages in compliance with GDPR
- Bulk email footer
- Unsubscribe and set preferences
for bulk mail - How to correctly forget a person's details
- Bulk Emails
- Contracts
- Partner in a contract
- Message patterns
- Groups of contacts
- Order overview for customer groups
- Directory or people and companies
- Contact per person or company
- Quickly available contacts
Finance management
System modules
System management
- moduleclientoptions
- digiSign
- formattedtexts
- System Configuration
- Processes in use
- Client
- Configure gateways for external messages
- Message with the outside world
- Email messages
- Secure business communication
- Send SMS directly from CRM
- Call directly from CRM
- Documents and files
- Additional functions with files
- Copying and moving files between objects
- Picture presentation
- Public link to the document
- Recent Files
- Dashboard
- Object location on the board
- Client items
- Revisions and comments
- Securing posts and internal discussions
- Translations
- Record Relationships
- Relation types
- sysrole
- User Processes
- System module
- System User
- User administration
- User Administration
- Secure login to the sytem
- Connecting users to VOIP PBX
- Secure Key Wallet
Framework
- frmobjectextension
- introhelp
- introhelp_mobile
- introhelp_aplikace
- versioninfo
- releases
- AyMINE modules and basic types
- cliplink
- introhelp_settings
- introhelp_deleting
- introhelp_dragdrop
- list_filtering
- AyMINE intro
- AyMINE access security
- AyMINE Modules
- Object locks
- System rights
- introhelp_keyshortcuts
- introhelp_shortcuts
- introhelp_icons
- list
- introhelp_generalinfo
- introhelp_objectdetail
- introhelp_objectlist
- introhelp_privateobjectnotes
- AyMINE User Rights Control
- introhelp_dashboard
Secure login to the sytem
Secure login must verify that the person accessing the system is actually the one who has
- Don't overestimate the quality of your password or the protection you have against getting it.
- Read more: Password is not enough for security
- The basis of security is multi-factor login
- Two-factor login options
- You don't have to do two-factor login all the time
- Installing in Chrome
- Selecting the application icon
- Android: Apka or installation via Chrome
Don't overestimate the quality of your password or the protection you have against getting it.
A password is not enough for a secure login. If your password is simple, it can be quickly discovered by brute force, i.e. by trying different options. Remember that computers are many thousands of times faster than you are. In the time it takes you to try a password, the robot will try dozens of them.
The system resists the robots, so it's not that simple, but in principle the model works and cannot be effectively resisted.
Read more: Password is not enough for security
Even a long password is not enough
Even if you have a password of, say, 20 nonsensical characters, you have to expect to enter it somewhere where an attacker will discover it. Just use a laptop somewhere under a camera controlling the area and the password can be read from your fingers by the camera operator. There are many other ways to get the password in a public space or on someone else's computer.
Practical example: student stole teachers' access to the school system
A playful and somewhat mischievous student in a school classroom plugged the keyboard of the class computer through a box that records everything that is pressed on the keyboard. The installation takes a few seconds, and because the computer wiring is tidy, there was no danger of anyone noticing the inconspicuous box.
Teachers rotate in the classroom, so several teachers log on to the computer in one day. It is even possible to tell from the timetables what order they log in, so there is no problem matching the recorded passwords to people.
The easily accessible box thus quickly gained access to the entire school network. Anyone can do the same, and even company laptops, which most people plug into a docking station with an external keyboard at work, are not immune. And while a student will use the cheapest device that they have to take away from the computer as well, professionals will use a sophisticated device that transmits data straight away wirelessly. So you never have to detect an attacker
Example from practice: Login credentials stolen by pizza supplier
Pizza delivery drivers are usually temporary workers who often spin their way into their jobs. Therefore, it is not a problem to be employed for a month and deliver pizzas in the vicinity of a particular company.
Especially in smaller companies, it is not uncommon for the delivery person to get to the office or wait somewhere for a while. The desktop computer at the reception is also a risk.
Back to the delivery driver: He took advantage of the moment and installed a tracking device with remote transmission. In offices where several people work, the inconspicuous items left on the cabinet went unnoticed and the device was able to get the data of one employee who was in the frame.
So the delivery companies don't stone us: Don't be afraid of the delivery men, the postman and the delivery men. But never assume they are reliable and vetted people and treat them accordingly. They shouldn't be unattended anywhere that something can happen. Delivery companies certainly won't vouch for them.
The basis of security is multi-factor login
Multi-factor login probably needs no introduction, everyone knows it from e-banking. What is its main advantage? The basic idea is that obtaining or revealing some information that moves through the public domain is not enough to gain access. Thus, entering data that can be revealed by a camera, keypad reader, or similar access may not be enough to gain access.
It is therefore fundamental to security that the login requires information other than that which you know and enter. Either a device that you have or access to another system to confirm your identity.
Two-factor login options
The system allows for two variants of two-factor login: via email or a more secure and convenient form of mobile phone biometric authentication.
Email verification
The basic method of second verification is a code sent to your email. After entering the correct name and password, you will be given a code to enter and only then will the system let you in.
The email authentication method is effective against brute force access detection, but may not be sufficient in a situation where someone is eavesdropping on your passwords, for example. In fact, it is very likely that they will also gain access to your email.
Mobile authentication
If you install a mobile app (Android only for now), you can authenticate access using your mobile phone.
Once you have entered your access, you will be asked to confirm the access in the mobile phone app, which will open a login request. We recommend using fingerprint authentication, which is convenient and gives the greatest assurance that it will never intercept the code you enter.
AyMINE does not collect biometric data
Even if your biometric data is used, the system does not collect and process this data. Identifying and verifying your identity is a matter for your mobile phone and the data never enters our system. It doesn't get from your phone, or even into our phone app.
You don't have to do two-factor login all the time
You probably use the system mostly from your laptop or personal device in general. We therefore recommend that you always use the same browser and set it to be a trusted device. The system will save it and you will be able to access from the same device and browser without authentication.
Install the app via Edge on Windows
We recommend installing AyMINE in windows – you'll have an even easier job.
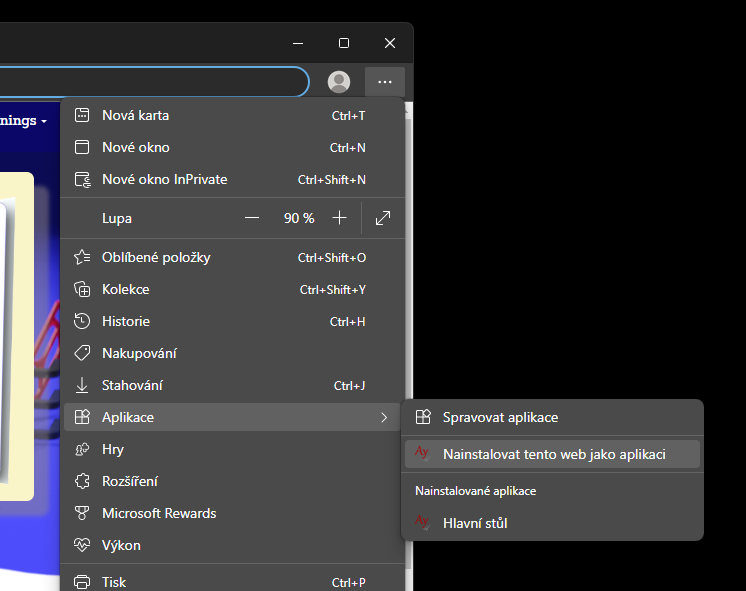
Installation Benefits:
- You have the option to put the app directly on your desktop or before startup
- The app remembers your login and saves you startup time
- You'll get notifications in the notification bar more easily because you can leave the app in the background. Don't close it with your browser.
- Installed AyMINE is safe Even after installation, AyMINE runs like an app in a protected web browser environment. It is thus 100% isolated from other data and programs on your computer, the data in AyMINE is protected from ransomware and your computer from potential risks from AyMINE
- Installed AyMINE is updated Unlike native apps, AyMINE is always updated. You'll never have to download an update. Just log out and the latest version will be released.
Not used to MS Edge? Never mind, the app behaves exactly the same in MS Edge as in other browsers. In addition, it won't mess around with other pages in your browser and you won't look for it.
Installing in Chrome
Chrome offers the same installation option – not only in Windows, but also on your mobile phone.
Installing AyMINE on your phone (Android / iOS)
You can install AyMINE via Chrome by following the steps described above – sign in to AyMINE and select install from the menu on your phone.
Selecting the application icon
Before you choose to install, you can select the application icon in the personal settings menu and choose which icon you want to use. The application will be shown with the icon you have chosen after installation. If you have AyMINE installed with multiple accounts, you can visually distinguish which installation is which.
Android: Apka or installation via Chrome
We recommend that you use Chrome installation on your mobile phone. Unlike Apka, you will always have the current version because the application will be updated when you log in. Apka cannot do this from the store, so you don't have the latest features available in it.