AyMINE – Technical documentation
Modules
Integration with ERP Abra Gen
 Task, project & quality management
Task, project & quality management
Manager approval with the task report
Why some data can't be deleted
Adminitration of areas, projects, calendars
Region / project / methodology
Change management process in a project
GDPR and record of qualifications
Qualification of user or contact
Right to Manage Qualifications
Failure Analysis for an Individual Property of a Component or Process
FMEA – Probability of Detection
FMEA – Probability of Occurrence
 Task, project & quality management
Task, project & quality management
Administration of the Task Management Module
System rights for the task management module
Improvements and Preventive Measures
Methodology and Quality Management systems
What a methodology / QMS consists of
Problems, tickets and their management
Collaborative Resolution of Multiple Problems
Customer Service Response Generation
Incident and Quality Issue Management
Objects affected by the problem
Problems, Incidents, Helpdesk Tickets
Return project plan by baseline
Sample tasks and methodologies of the area
Effect of the task on the right to modify the attached object
The person responsible for the task
Working procedure – task definition
Management of responsibilities - RACI Matrix
Objects related to the task pattern
 Contacts and directories module (CRM)
Contacts and directories module (CRM)
Order overview for customer groups
 Contacts and directories module (CRM)
Contacts and directories module (CRM)
System Permissions and CRM Module Settings
Send bulk messages in compliance with GDPR
How to correctly forget a person's details
Unsubscribe and set preferences
for bulk mail
 Web management and automation
Web management and automation
Receiving a message from the web
Human resources
Personalistics – User Permissions and roles
Human Resources module security
Manage department / division data
Overview of Personnel Information for pracov# Employment Contract
Synchronizing staff and system users
 Products, assets and sales
Products, assets and sales
Manage the Property & Business module
Why are the Quality criteria usefull
Received order for goods or services
Managing Finance
Metrics and Measurements
Work summaries from generated data
Technical Modules
Sabre plugin module
Enterprise Architect connector
Database link to Enterprise Architect database
Enterprise Architect connector
System Modules
 The AyMINE Framework Module
The AyMINE Framework Module
AyMINE — Tips for Mobile Usage
Configure how your system looks and works
Gestures and Keyboard Shortcuts
More about how the system works
Private notes and tags for objects
Overview of Modules and Record Types
Filtering in the list of records
 System Management
System Management
Additional functions with files
Copying and moving files between objects
Files (documents) linked to the object
Formatted texts in the application
Gateway settings for external messages
IMP gateway settings for email communication
Internet Call Gateway Settings
Message with the outside world
Trusted user device
Trusted device is a device that user confirmed to be safe for use without two-factor authentication
System allows you to mark your device (typically your own mobile phone or notebook) you are working as a trusted device. Trusted device:
- Simplifies login because it does not require two-factor authentication
- Support work with private encrypted information and allows work with vault for passwords
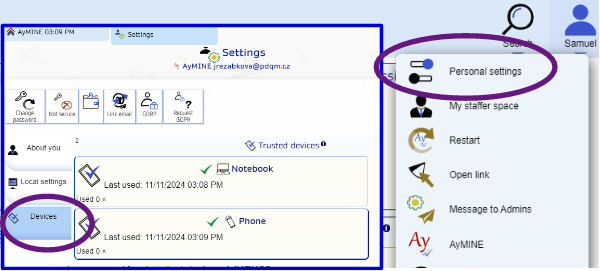
How to mark device trusted
- Login to the application using two-factor authentication
- Go to the user settings and start trusted device confirmation
- Check your email for verification code
- Enter the code from email
- Login again to the system – last confirmation that everything is made by you
After all steps device is marked trusted.
How to clear the settings
Remove “trusted device” from a device that you are currently using
If you mark your computer trusted you have Untrusted button in the user settings. Using the function change the settings.
Reject “trusted device” mark remotely
You can also remove “Trusted” mark remotely. All trusted devices are visible on the page of trusted devices in user settings. You might remove any device from list.
System administrator can remove you trusted device
Remove “trusted device” mark from any device could also make a system administrator. E.g. when you loose your mobile with private access, call your administrator. When he remove the mark, no one can access the application or even open password vault and access encrypted notes.
What a safe device allows
On a safe device it is possible to:
- Save your login in a more secure way than in a browser.
- Save passwords to unlock encrypted content
- Save data for offline access (requires an app)
You should know
The system will still occasionally log you out
The system may cancel your login for several reasons. The most common reasons are:
- The system has been updated and it was necessary to cancel saved logins (the system will log you out when it downloads updates).
- Your browser has cleared your saved data, and with it has removed data that is necessary to verify where you are.
Trusted device is browser-dependent
When you mark your device “trusted” in a browser (e.g. the FireFox), that’s valid only in that browser. When you use another one (e.g. Chrome) computer won’t be trusted.
Recommendation – install AyMINE as an application
Install AyMINE in windows via the Edge browser. You’ll get more safe access without mixing AyMINE with other browser windows.
- Start MS Edge and login to the system
- Use “add application” in the Edge menu.
- You can add AyMINE application from the start menu to the dashboard or main panel
Trusted system stores password vault
Only trusted computers are allowed to use the vault – stored passwords for access encrypted notes. Untrusted computer never gets data about your vault.